CAL Defense - Lifetime deal is out . Click Here
Welcome To Cyber Aeronautycs Ltd.
SECURING AIR & GROUND INFRASTRUCTURE
We are an aerospace and defense company in Bangladesh and engaged in research, design , development, manufacture, integration and sustainment of advanced technology systems, products and services.
Secure Your Business Against Modern Cyber Threats
Data isn’t just another resource — it’s integral to your daily operations. CAL Defense solutions safeguard you against data loss, security breaches, operational downtime, and the financial and reputational harm associated with each.
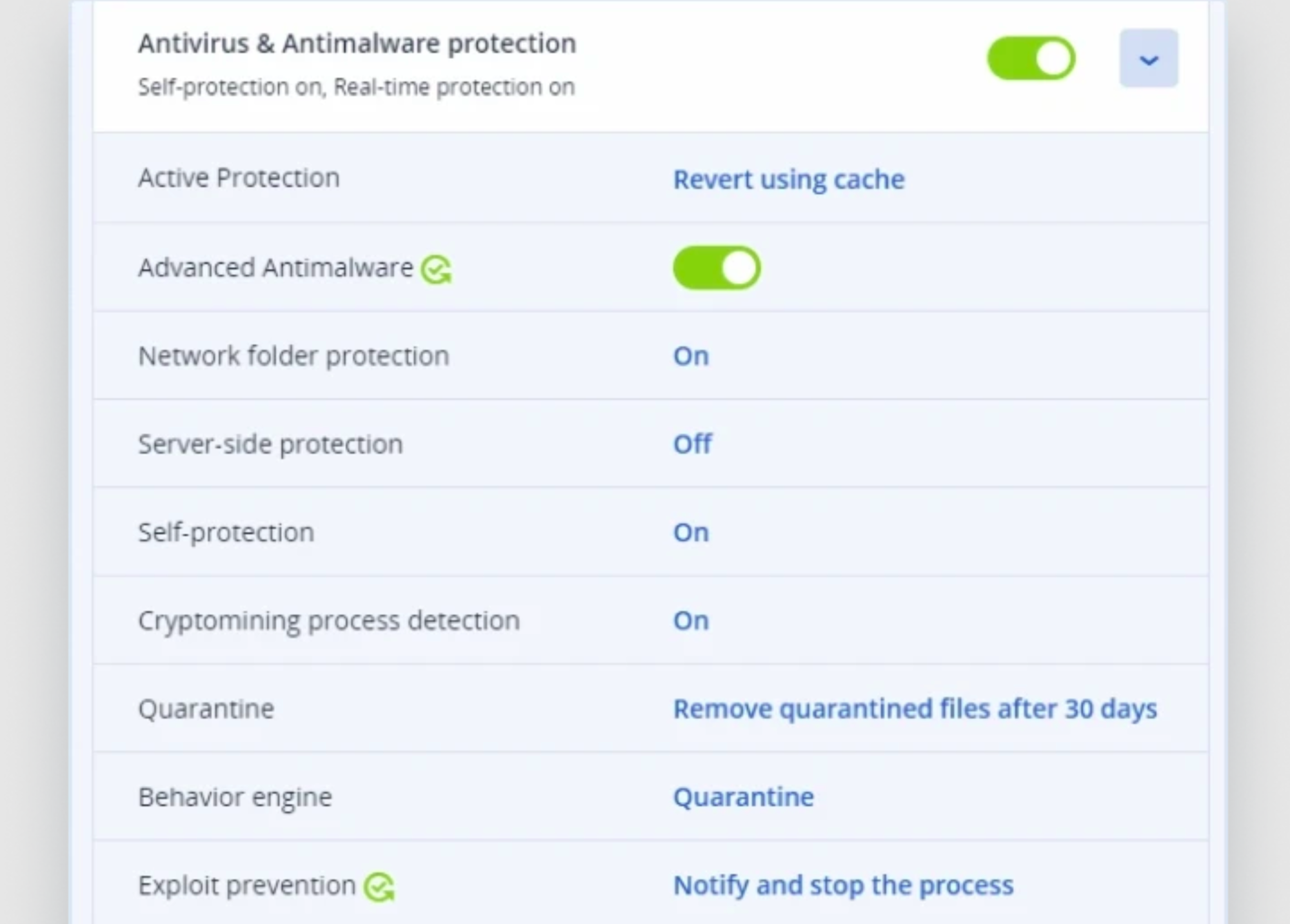
Superior Cyber Protection
Cyberthreats are evolving at an incredible rate — and simple data backup and cybersecurity tools are no longer enough to contain them. CAL Defense is all-in-one cyber protection solutions combine cybersecurity, data backup, disaster recovery, and more to ensure the integrity of the data and systems you rely on.
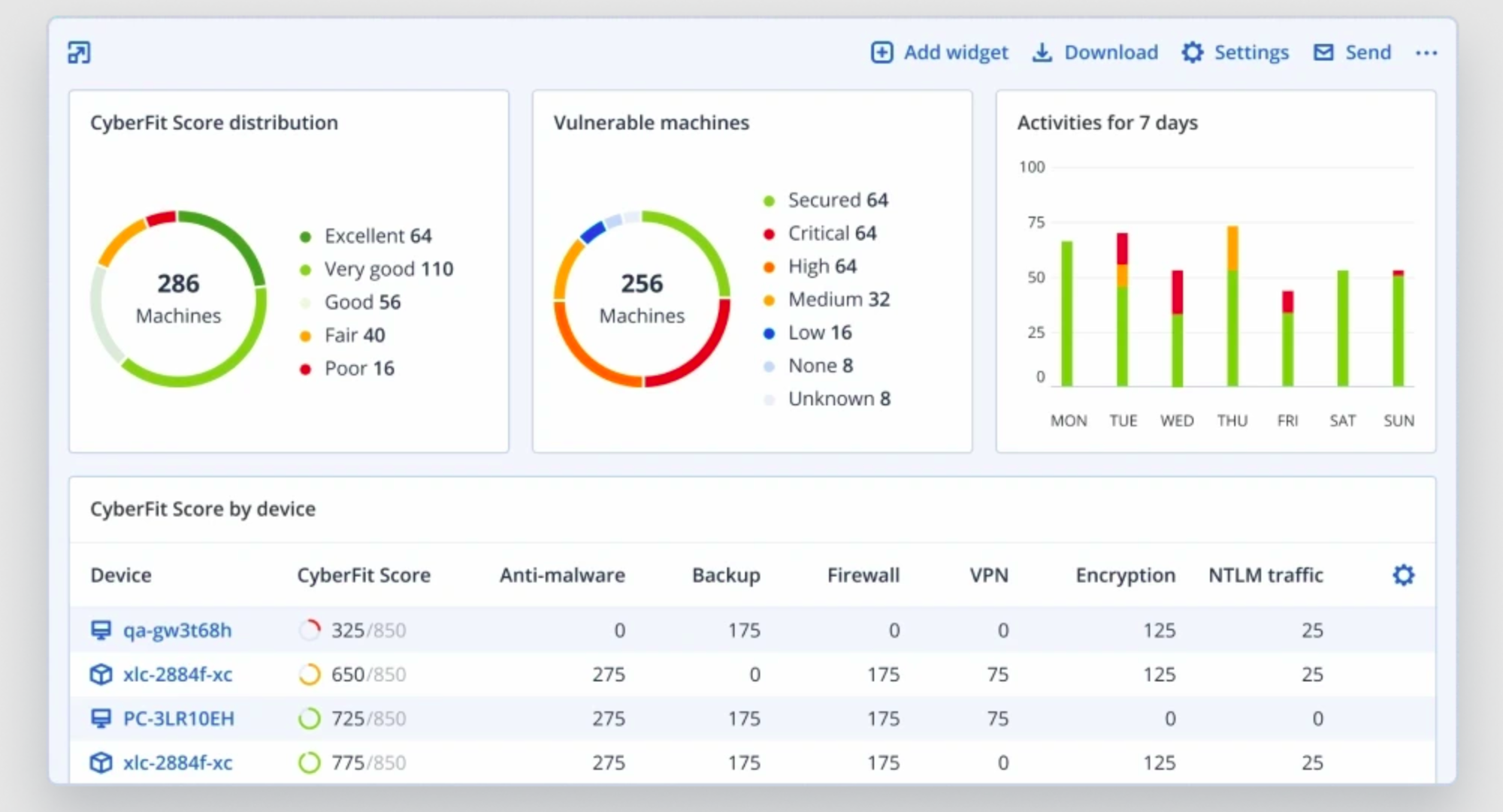
Reduce Complexity
If you’re like other businesses, you probably use a complex patchwork of solutions to defend against data loss and other cyberthreats — but this approach is tough to manage and leads to security gaps. CAL Defense integrated cyber protection solutions safeguard entire workloads with greater efficiency and a fraction of the complexity, freeing up resources and enabling you to focus on protection and enablement rather than juggling tools.
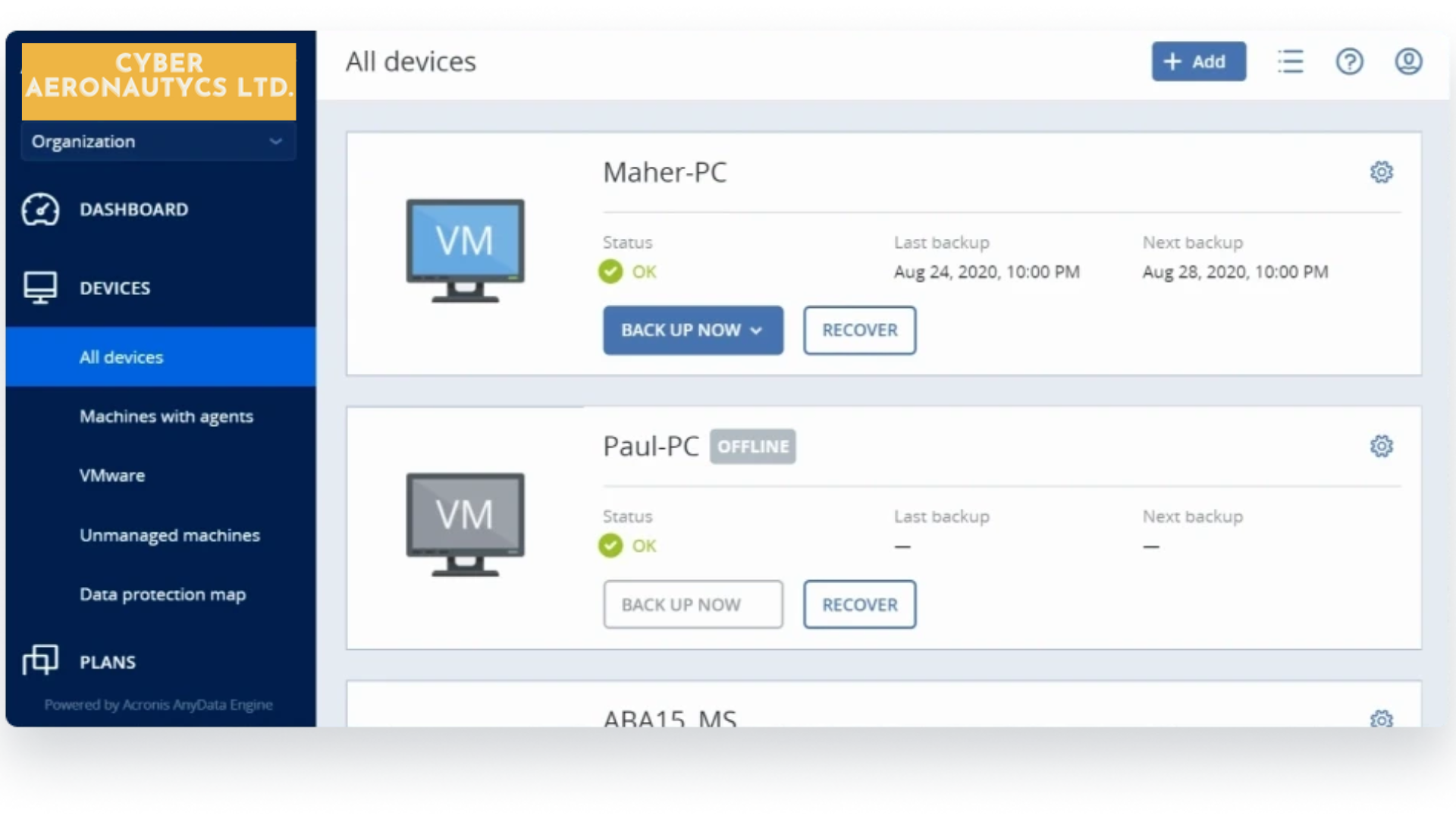
Simplify Deployment & Management
Protect entire workloads without the friction. Getting started with CAL Defense solutions is simple and painless. Provision multiple systems with just a click, and manage everything — from backup policies to vulnerability assessments and patching — through a single pane of glass.
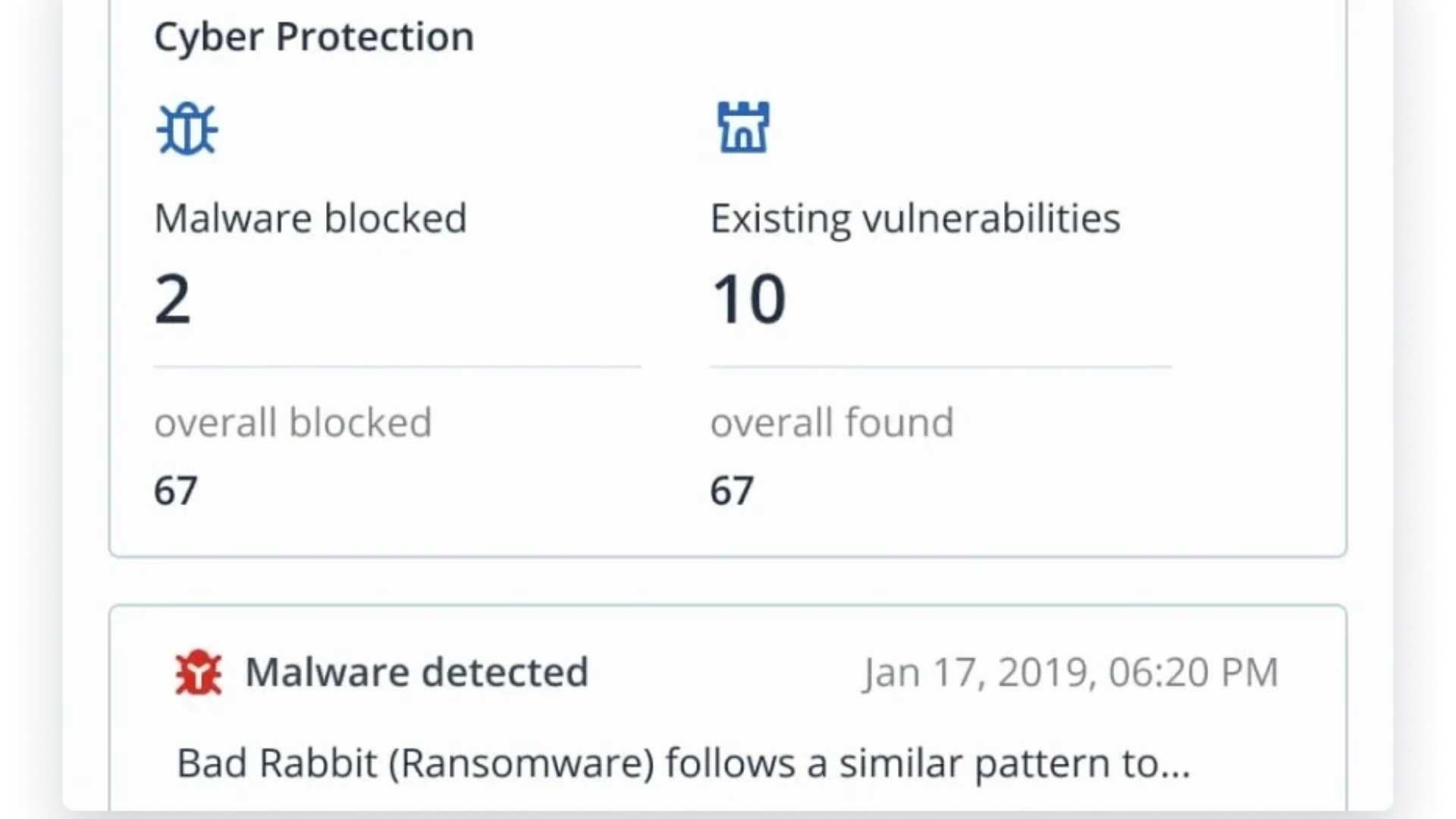
Safeguard against any threat
Effortlessly detect and block cyberthreats — even those never seen before. CAL AI-driven behavioral heuristic engine identifies the malicious processes that malware relies on, delivering best-of-breed protection with fewer false positives. In third-party tests from industry leaders like AV-TEST and Virus Bulletin, CAL solutions have demonstrated a 100% detection rate with zero false positives.
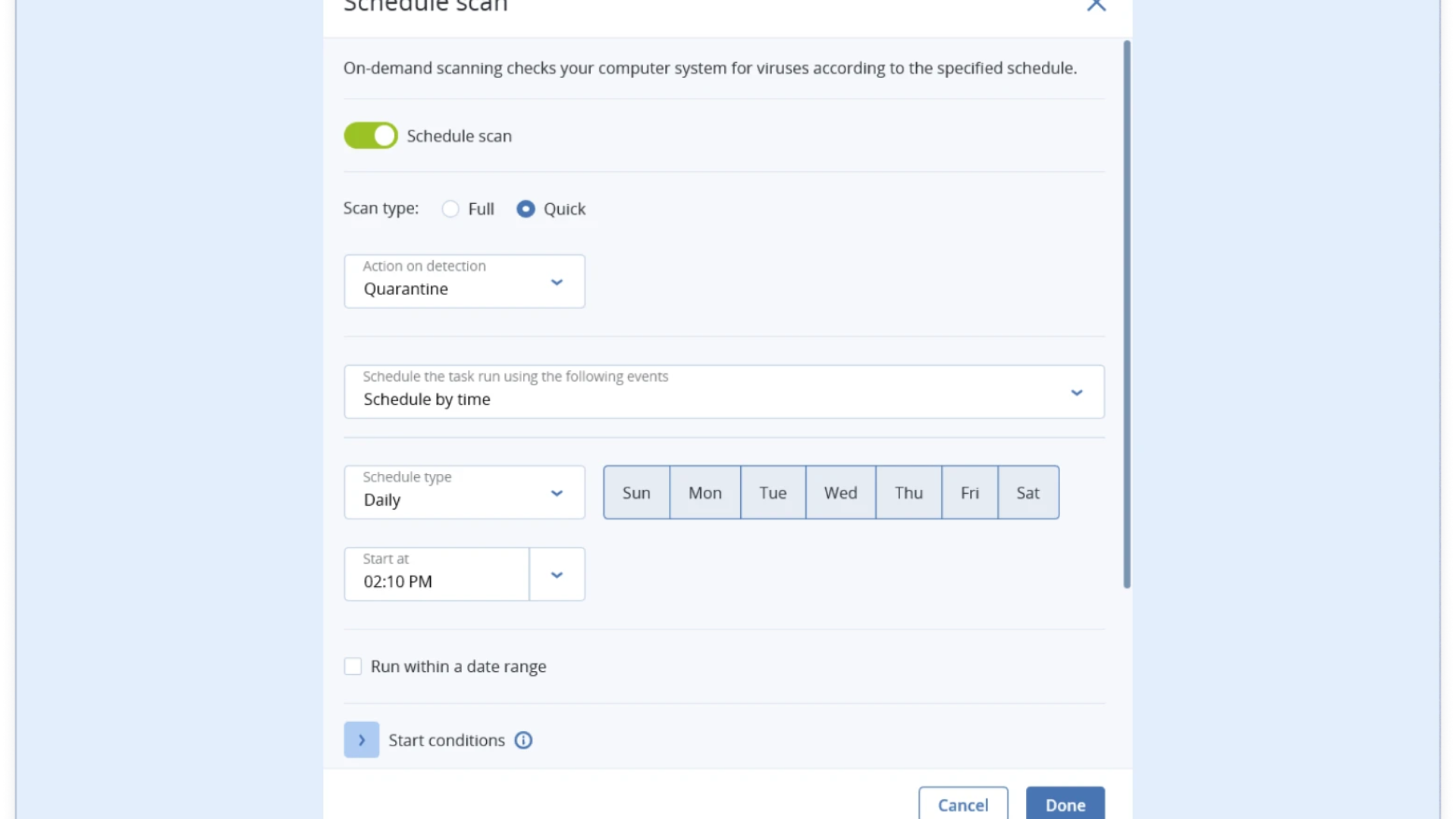
Ransomware protection
Data has become the world’s most important resource, and cybercriminals are extorting organizations around the world for theirs every day. Ransomware threatens your customer and employee data, trade secrets, even your business’s very existence. CAL solutions use next-generation cyber defense to stop ransomware in its tracks — even variants that have never been seen before.
Ensure Operational Resiliency
Modern businesses face an onslaught of cyberthreats. New forms of ransomware emerge every day, and automation enables attackers to target countless businesses with ease. Data breaches and downtime caused by ransomware can be catastrophic to an organization’s health, which is why CAL solutions take a multilayered approach — blocking ransomware and other cyberthreats while also supporting disaster recovery and forensic analysis.
Protect Your Reputation & Bottom Line
After a ransomware strike, cybercriminals may demand hundreds of thousands of dollars — even millions. Whether you pay or not, these numbers are often dwarfed by the unavoidable spillover impact to your organization. Severe reputational damage, regulatory fines, and loss of trade secrets can all result from data breaches. CAL next-generation anti-ransomware solutions block both known and unknown threats — preventing disaster from striking your business.
Ensure Comprehensive Cyber Protection
As your employees demand more from their IT services, it’s all too easy to wind up with a complex patchwork of tools — one that’s tough to learn and tough to maintain. CAL all-in-one solutions integrate anti-malware protection with data backup and endpoint protection management. This unique approach eliminates protection gaps and enables seamless remediation — no need to juggle multiple solutions.
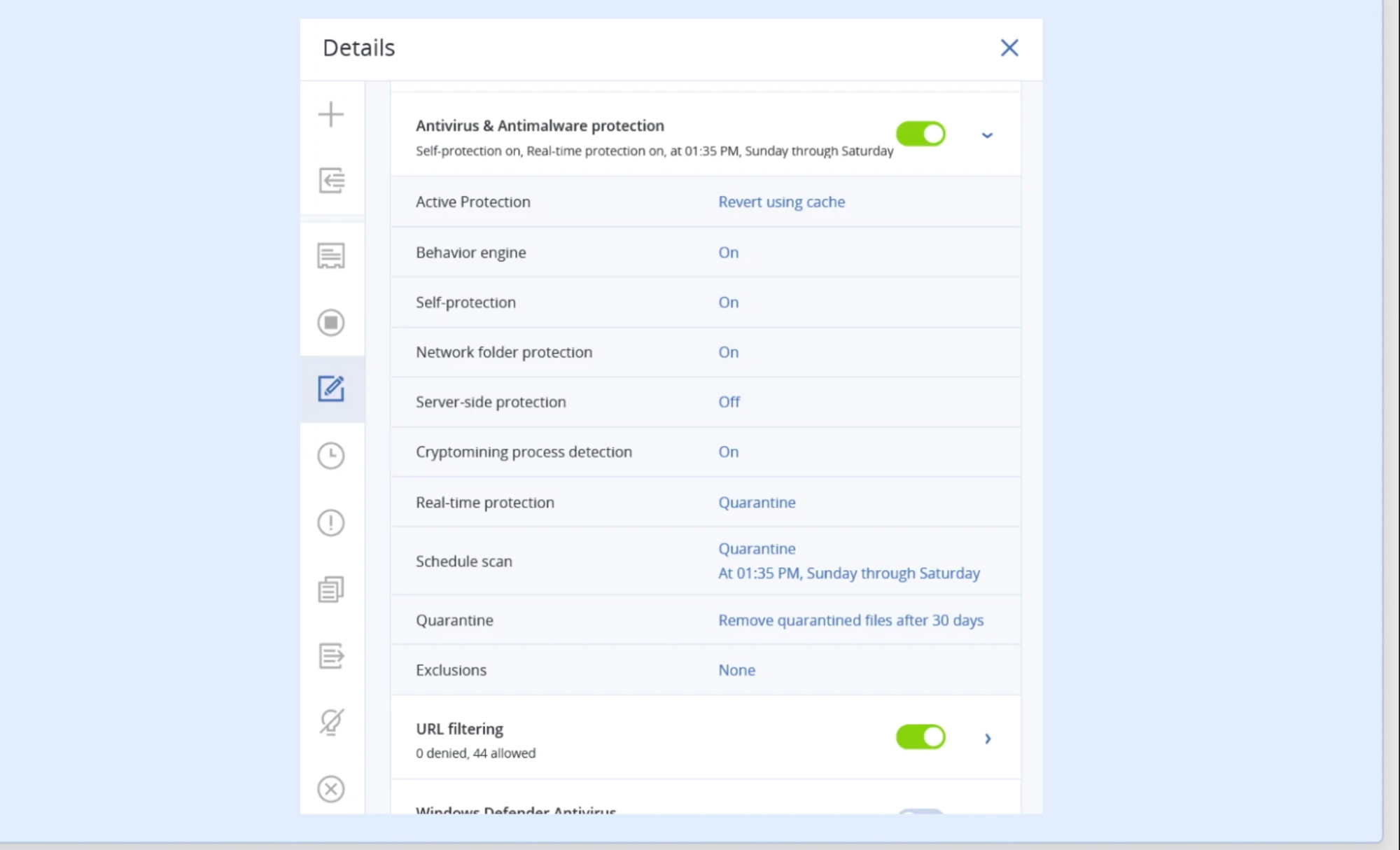
Anti Malware For Corporate Environments
Malware — malicious software that’s designed to damage systems and steal data — is a pervasive and growing cyberthreat. Cybercriminals strike at businesses every day in the hopes of extorting ransom payments or stealing sensitive information. CAL anti-malware protection solutions use next-generation techniques to effectively halt both known and unknown types of malware in their tracks.
Identify & Block Cutting Edge Cyberthreats
Many companies rely on signature-based detection to fight malware, blocking programs that appear on a list of known threats. But this approach can’t keep up with the modern landscape: new malware variants emerge constantly, and their average lifetime is mere days. CAL next-generation solutions use behavioral analysis — powered by machine intelligence — to halt the malicious processes that malware relies on, keeping your business safe from known cyberthreats as well as those never seen before.

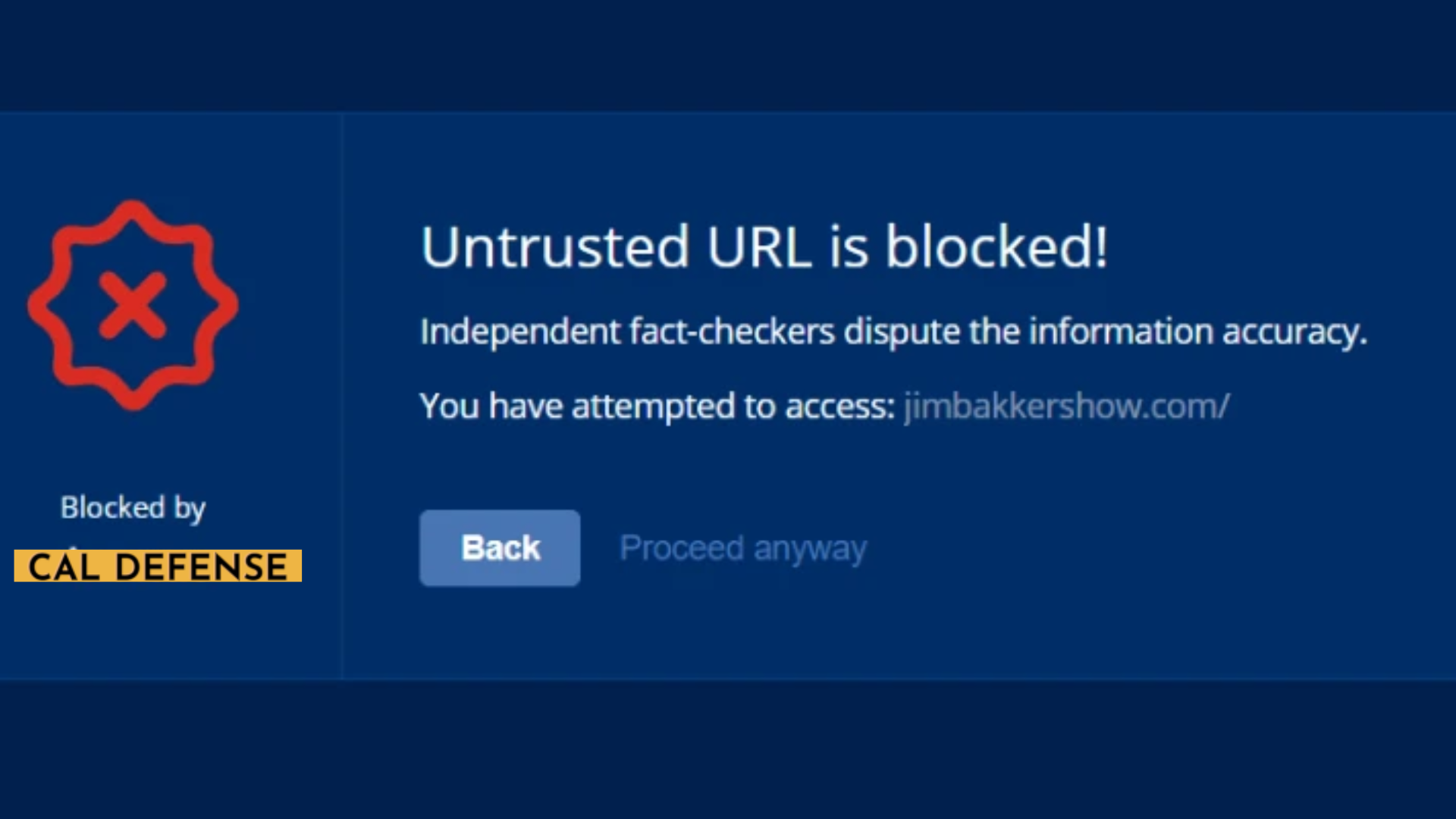
Stop Malware At The Source
Nearly all malware is distributed through the internet — preventing it from even reaching your systems is one of the most effective defenses possible. CAL solutions take a multilayered approach to cybersecurity, with URL filtering functionality to block user access to malicious websites and HTTP/HTTPS request interception to stop drive-by downloads that might otherwise go unnoticed. Detection rules are updated on a continuous basis based on ongoing threat intelligence gathered by us and our industry partners.
Advanced Data Loss Prevention (DLP)
Current DLP solutions require costly security expertise and deep knowledge of clients’ business processes, together with complex, error-prone, manual configuration to ensure client-specific policies. With Advanced DLP, you can prevent data leaks for clients with the provisioning speed and policy-management ease you need.
Automated DLP Policy Creation
Minimize manual work and the risk of errors. Simplify provisioning by automatically generating an initial DLP policy for each client.
Client Specific DLP Policies
Monitor outgoing sensitive data flows across organizations to automatically map clients’ business processes to a DLP policy — adjusted to their specifics. Leverage optional end-user assistance for higher accuracy, and request client validation before enforcing a policy.
Comprehensive Array Of Controlled Channels
Control data flows across local and network channels, including removable storage, printers, redirected mapped drives and clipboard, emails and webmails, instant messengers, file sharing services, social networks, and network protocols.
Unmatched DLP Controls To Differentiate Your Service
Ensure web-browser- independent control of data transfers to social media, webmail and file-sharing services. Leverage content inspection of outgoing instant messages and sensitive-data detection in images on remote and offline computers.
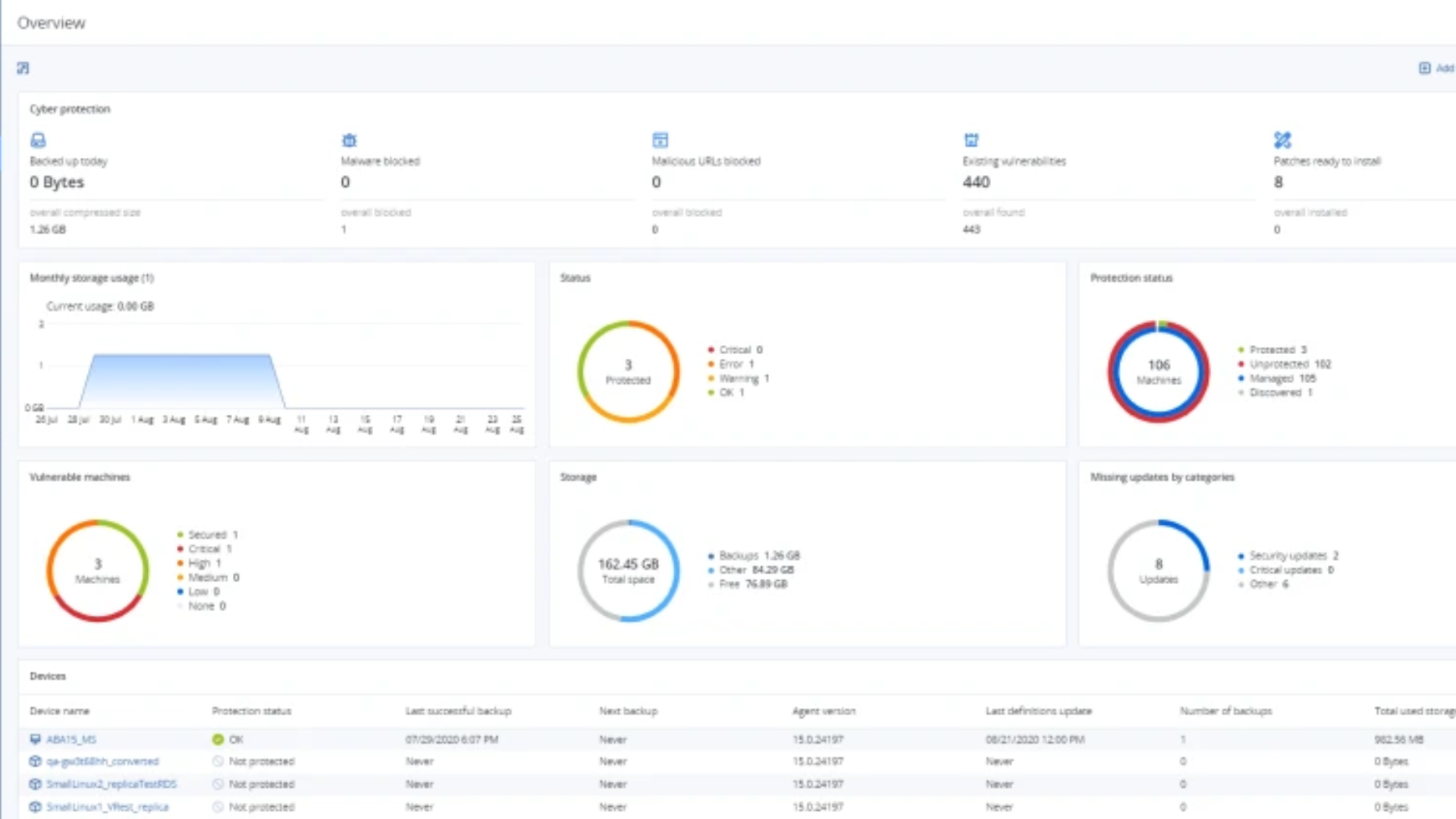
Centralized cyber protection with single console
Control your TCO, reduce management overhead and boost margins by using a single solution that integrates backup, disaster recovery, next-generation anti-malware, email security, workload management, and data loss prevention.
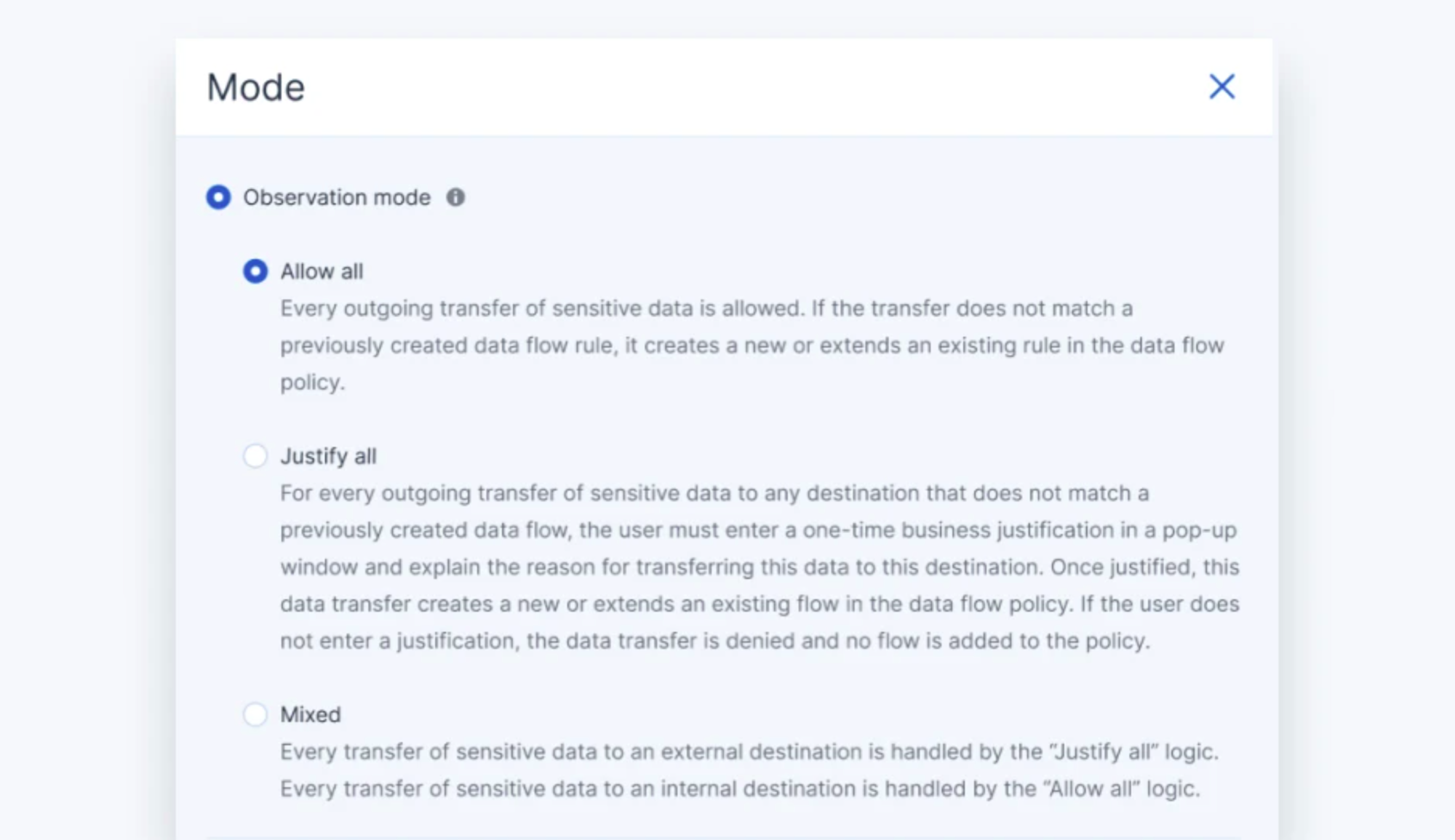
Effortlessly provision DLP services with an observation mode
In the observation mode, the agent monitors clients’ endpoint computers for outgoing, sensitive data flows to generate the baseline DLP policy automatically or, alternatively, with end-user justification of the riskiest data transfers.
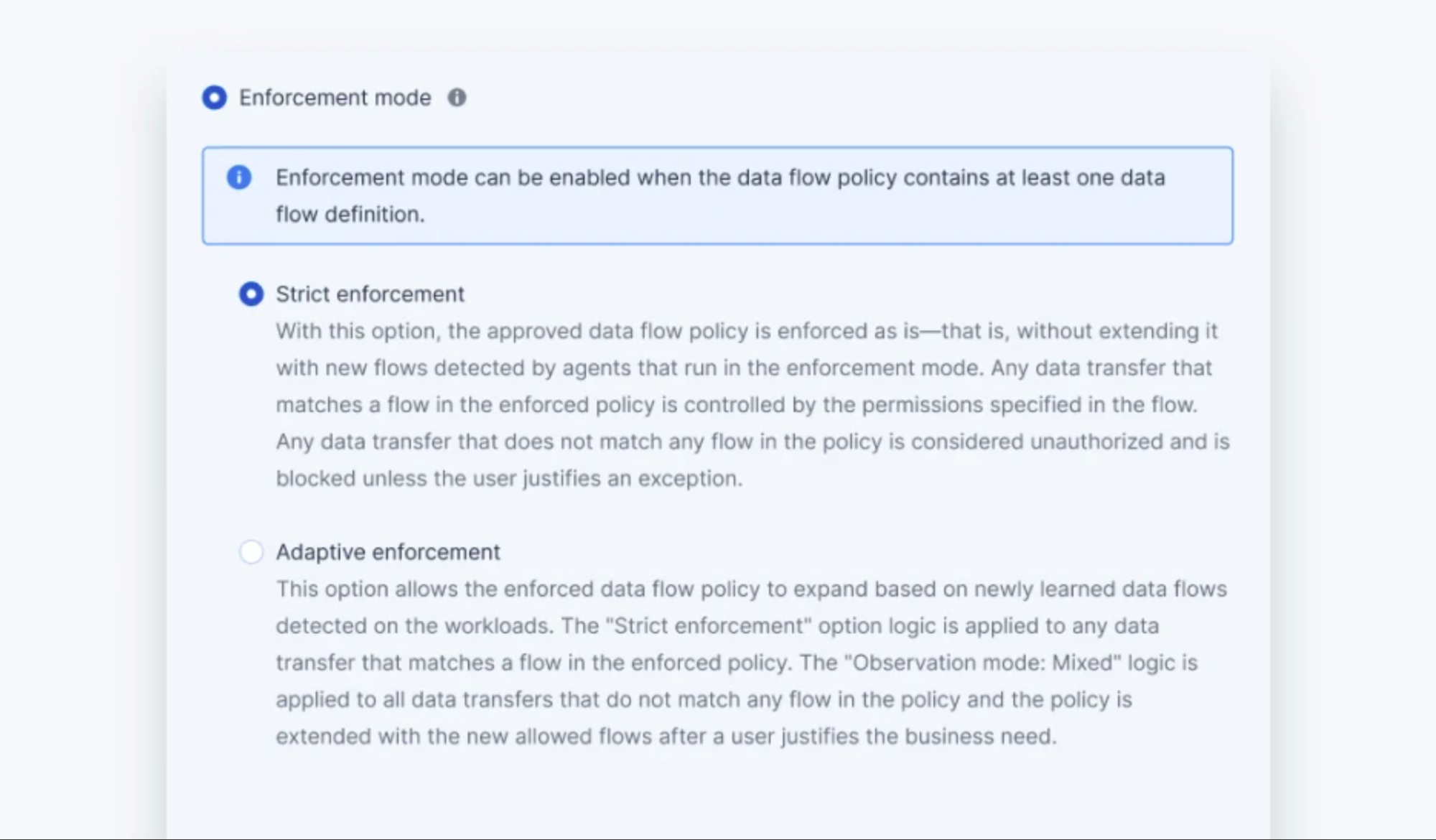
Reduce management burdens with multiple DLP policy enforcement options
Once the DLP policy is validated with clients, you can enforce it to start protecting their data. Enforcement mode enables you to select how to enforce DLP policies:
- Strict enforcement — enforces the DLP policy as defined, without extending it with new data flow rules. Any data transfer that doesn’t match a defined data flow rule in the policy is blocked unless the end user requests a one time business-related exception.
- Adaptive enforcement — enforces the DLP policy but offers flexibility by automatically extending it with new rules for allowing previously unobserved business-related data flows.
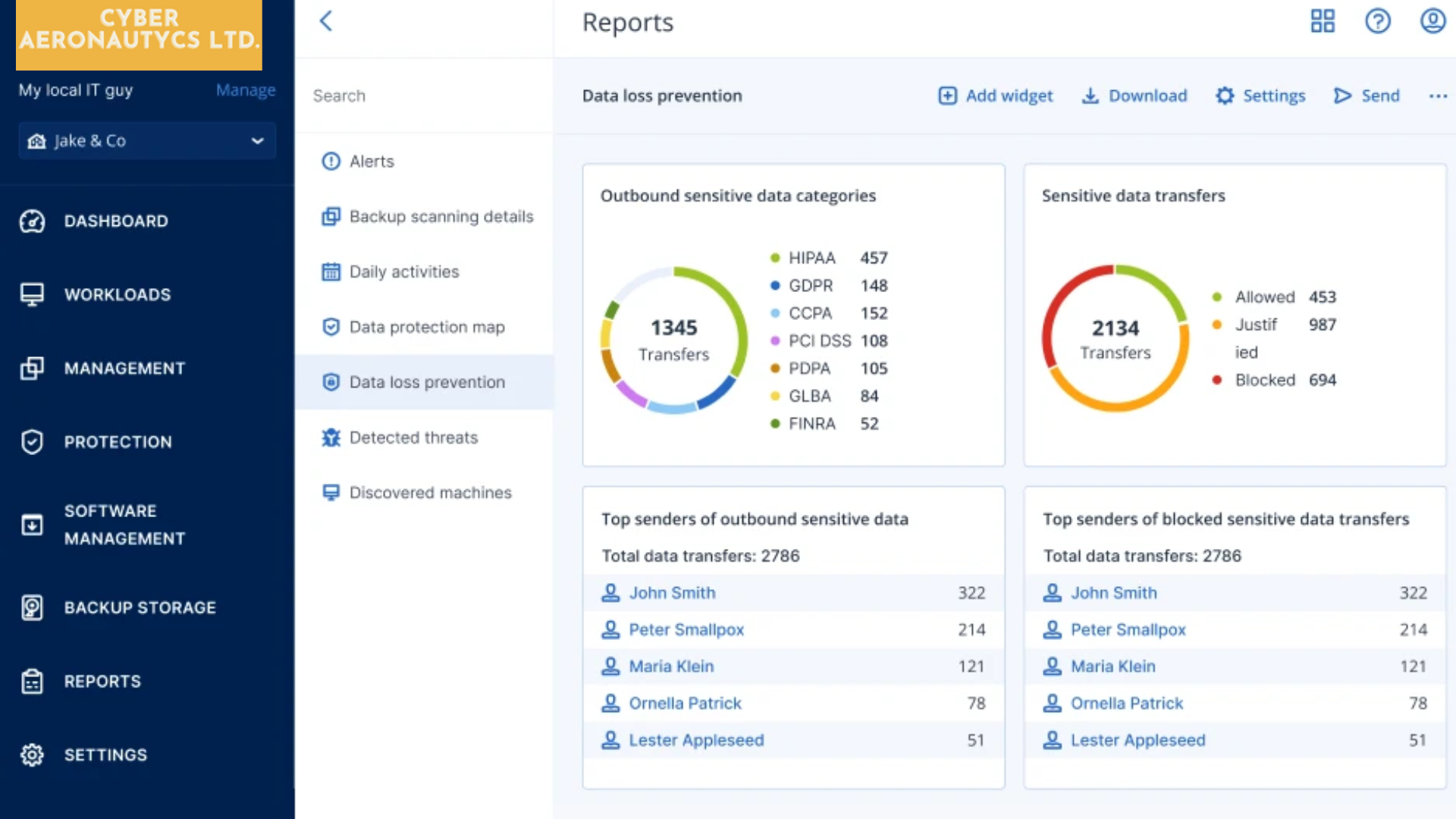
Demonstrate your value to clients with powerful widgets
Enable ongoing reporting to clients with powerful widgets, that demonstrate the value of your DLP services. Provide service technicians and clients with visibility into blocked sensitive data flows; most active data senders; users with most blocked data transfers; and all sensitive data transfers split by category (blocked, allowed or justified).
Automated patch management
From employee workstations to servers, it’s important to keep your business-critical systems up to date with the latest software patches. New vulnerability fixes are released frequently, but managing all these updates can be challenging and time-consuming. CAL Defense automated patch management solutions make it easy to protect your business against the latest cyberthreats.
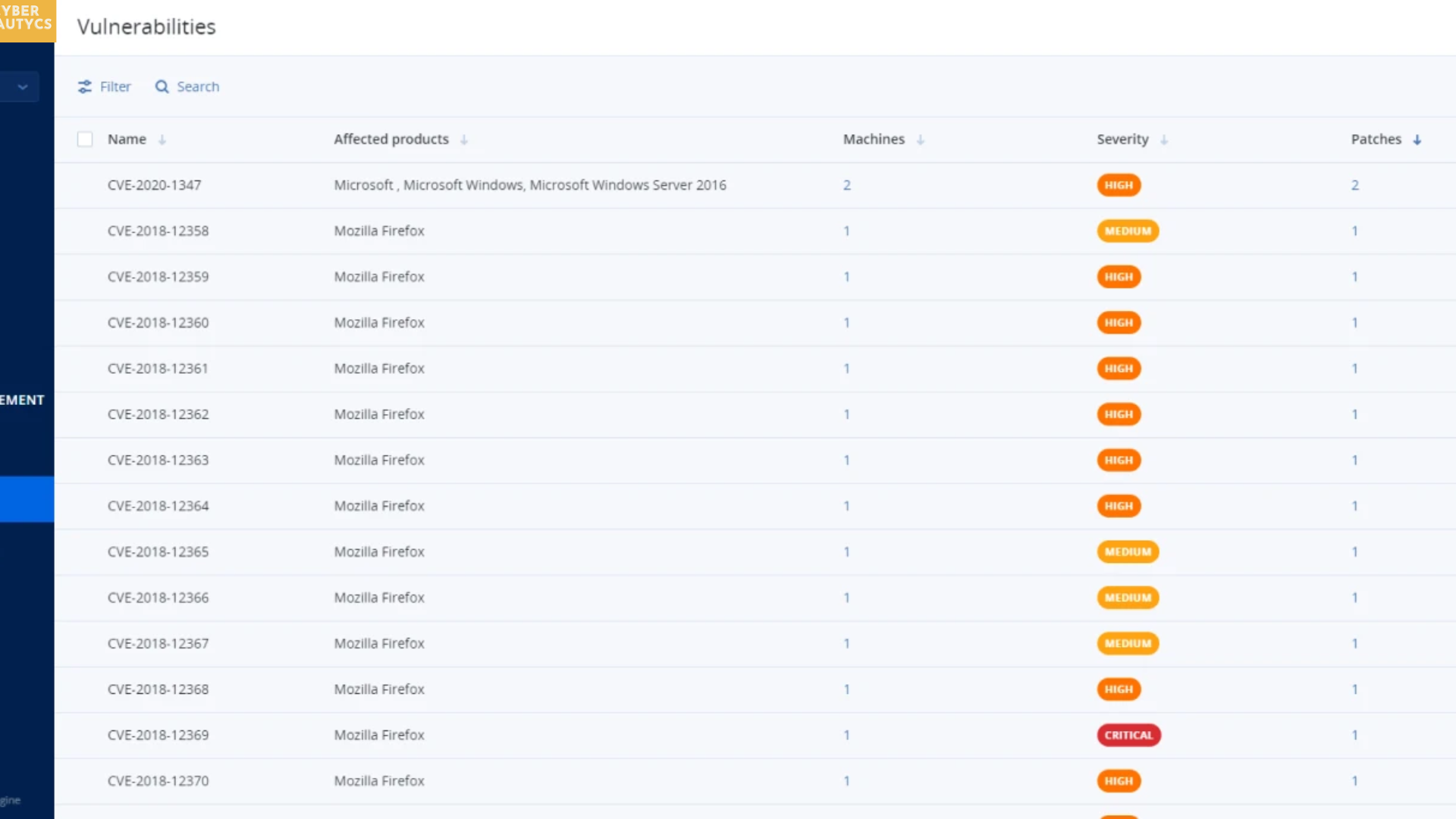
Close Vulnerability Gaps With Proactive Protection
Every day, patches are released to fix newly-discovered vulnerabilities in popular software tools. But until these fixes are actually installed — on all of your systems — your business remains vulnerable to cutting-edge cyberthreats. CAL integrated vulnerability assessments help you to identify systems and applications that require updates, and to easily roll out patches on-demand or according to a schedule — all through a single, intuitive dashboard.
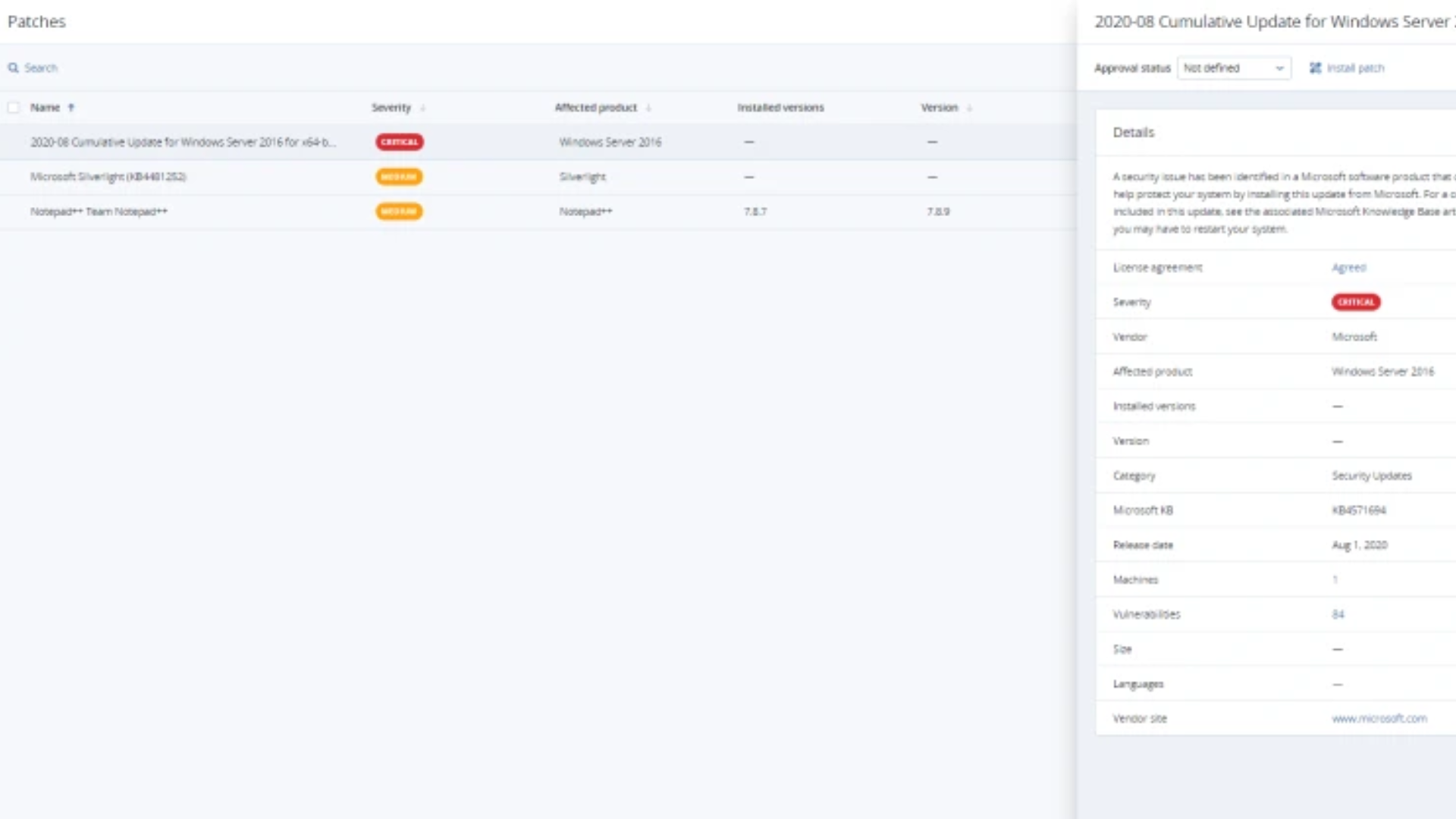
Keep Your Systems Operational With Fail-Safe Patching
It’s rare, but even well-tested patches can introduce problematic bugs or incompatibilities with your other software. That’s why CAL solutions automatically create full-system backups before applying any new patches — protecting business-critical data and making it quick and easy to roll back your computers to a known working state, should the need arise.
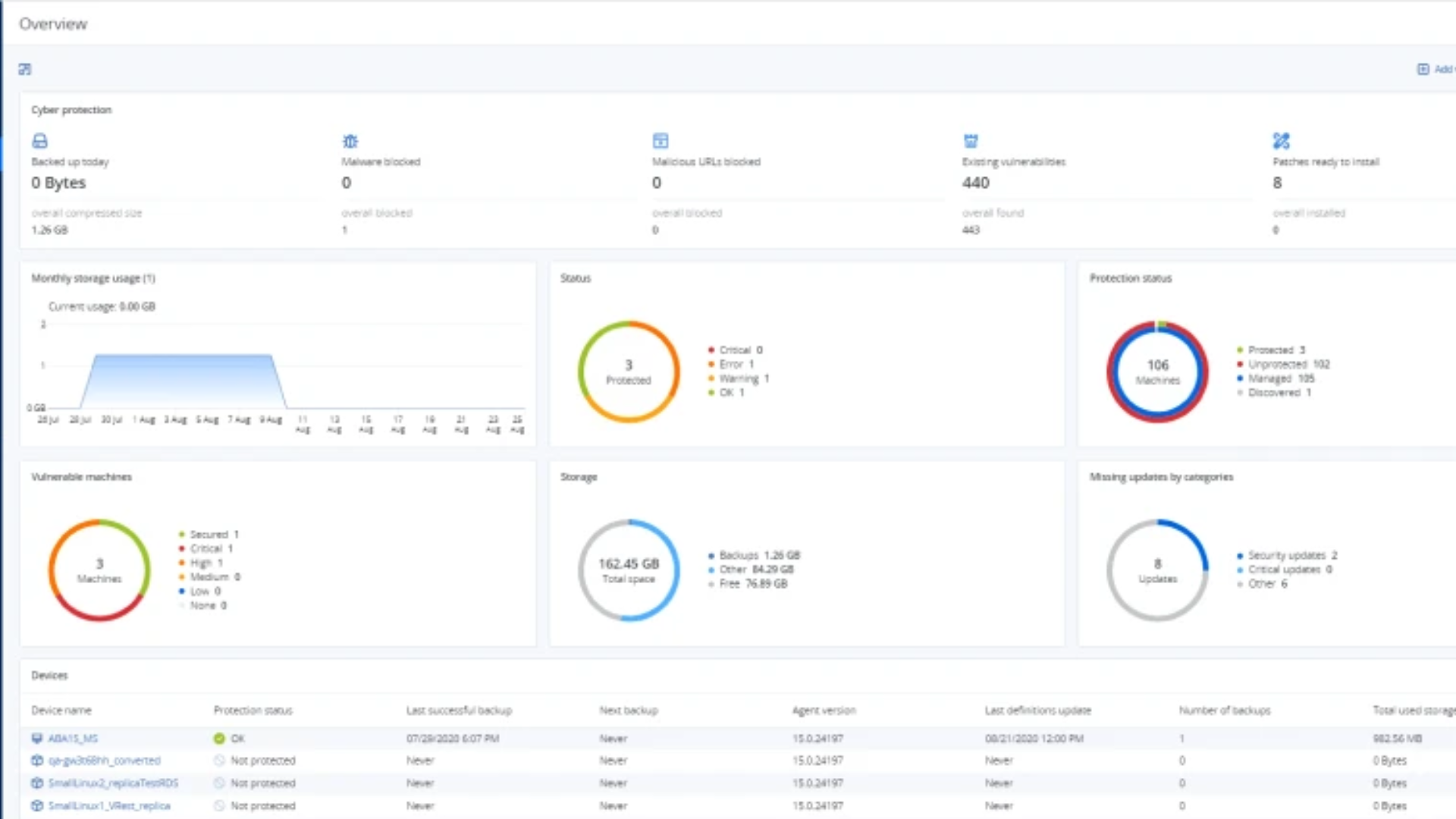
Ensure Comprehensive Cyber Protection
As your employees demand more from their IT services, it’s all too easy to wind up with a complex patchwork of tools — one that’s tough to learn and tough to maintain. CAL all-in-one solutions integrate anti-malware protection with data backup and endpoint protection management. This unique approach eliminates protection gaps and enables seamless remediation — no need to juggle multiple solutions.
Best In Breed Enterprise Grade File Backup & Recovery
Today’s businesses rely on data like never before, making its protection essential. From cyberattacks to hardware failure to user error, any threats to data integrity have the potential to devastate your organization. CAL file backup and recovery solutions draw on the power of integration to deliver unparalleled data security, protecting your organization’s operational continuity, reputation, and bottom line.

Preserve Backup Integrity
The world of cyberthreats evolves quickly — so should your approach to file backups. Criminals now target backups specifically in an attempt to prevent easy recovery, increasing their leverage over victims. CAL solutions integrate data protection with threat-agnostic cybersecurity, enabling unique interactions like the scanning of backups for malware and ensuring that you’ll always have clean and accessible copies of business-critical data.
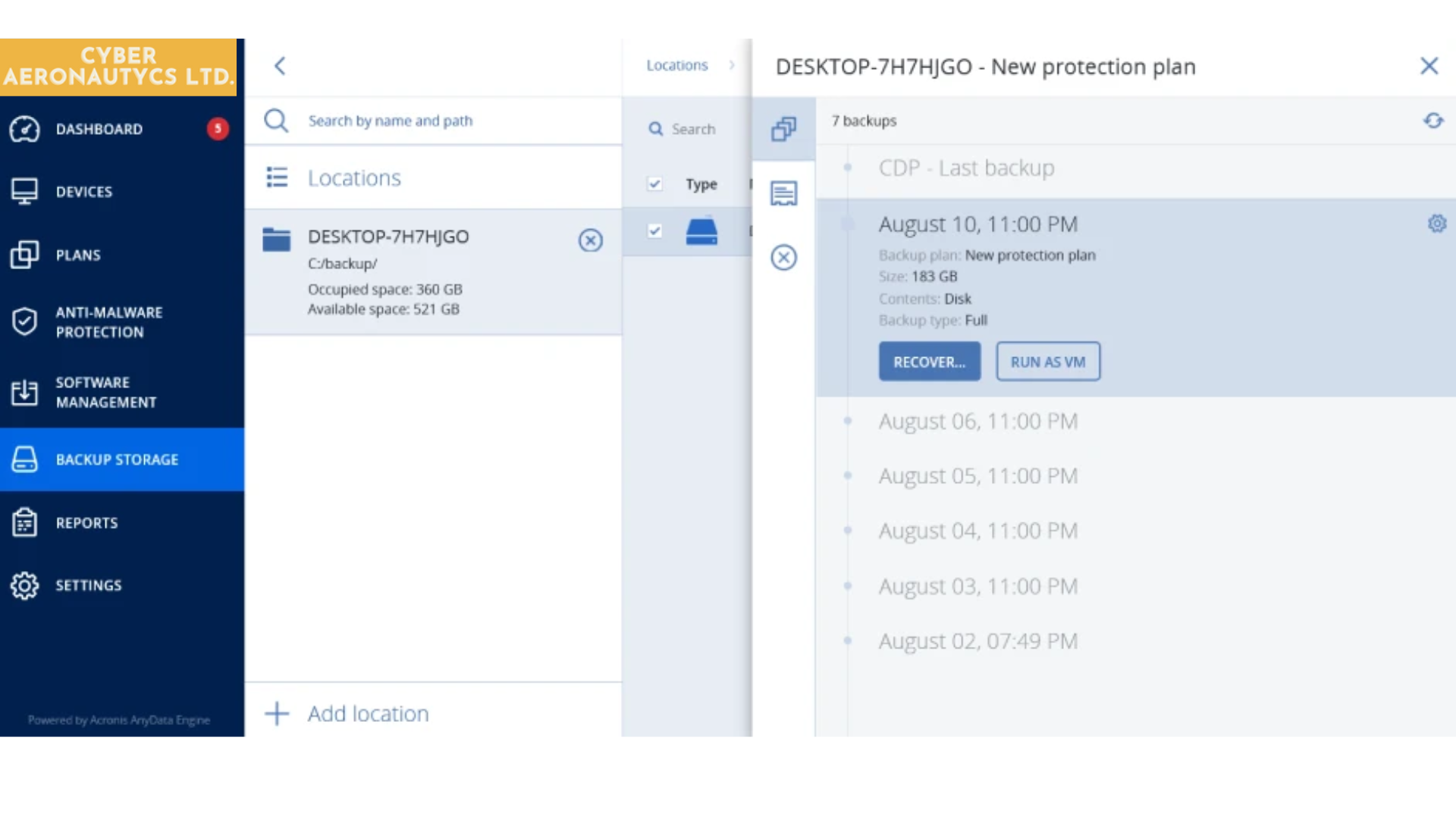
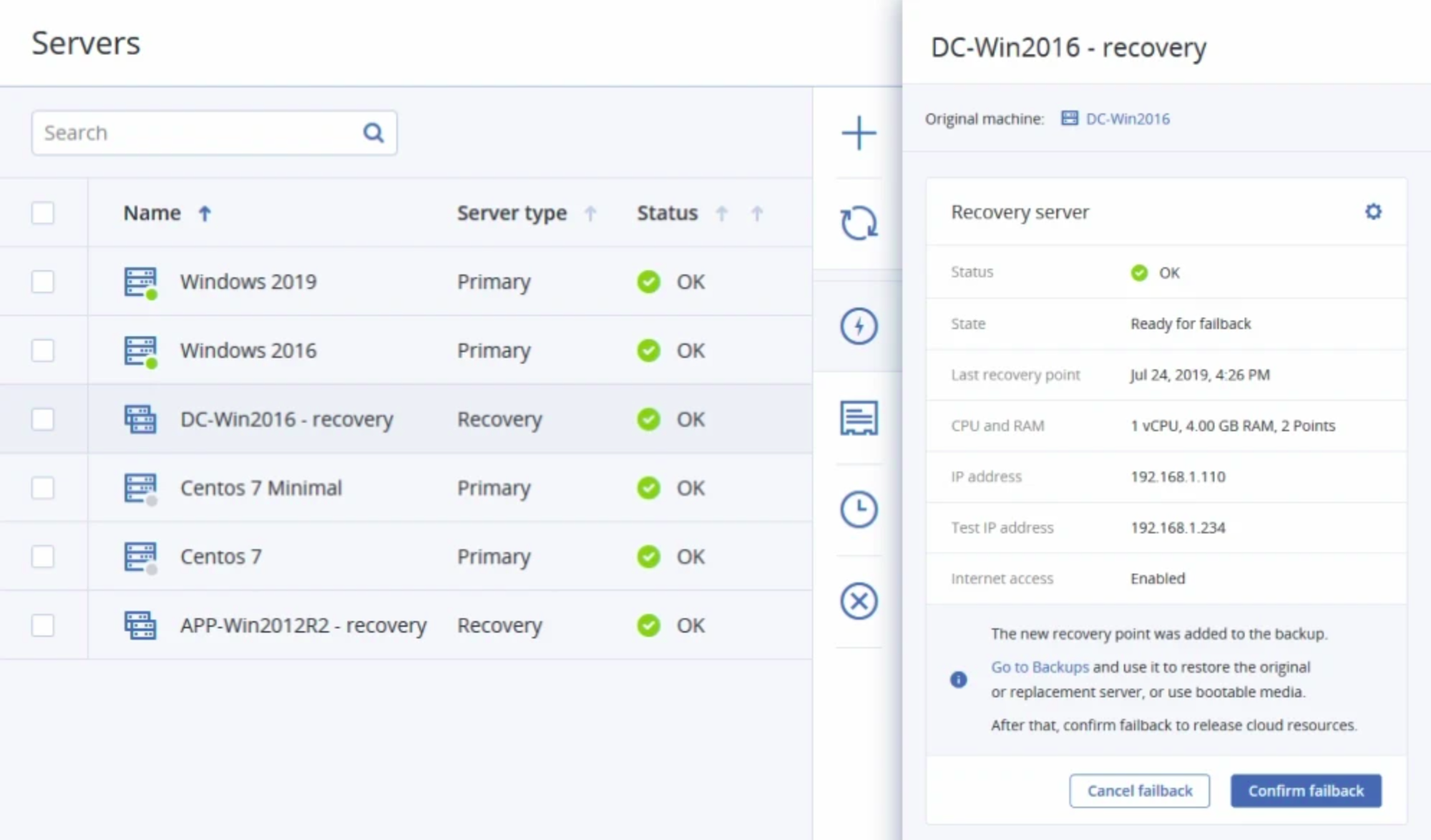
Recover Within Minutes
When disaster does strike, every second counts. Downtime and data loss are expensive prospects for any business, and can lead to lost sales, reputational harm, even regulatory fines. CAL Defense agent monitors and backs up all changes to critical applications and files in real-time, allowing you to choose a recovery point just seconds before the incident occurred, while CAL Instant Restore enables industry-best RTOs by immediately launching your backup as a virtual machine.
IT Disaster Recovery
Expect the unexpected - Avoid business disruption with world-class recovery options.
Minimize Downtime & Maximize Productivity
Every bit of lost data or minute of downtime can be tragic. Data is growing at approximately three times the rate of IT staff. On average, downtime can cost $5,600 per minute. That combination can be detrimental to a small or medium-sized business. You need to proactively protect your business-critical data, applications and systems, and the faster you can recover, the better. From backup with rapid restores to full disaster recovery, CAL Defense enables you to avoid business disruption.
Rapid Recovery For All Workloads
CAL Defense is the answer to help you meet your rapid data recovery needs – with out-of-the-box RTOs and RPOs of under a minute to an optional automated cloud-based disaster recovery implementation for critical apps.
Experience World Class Recovery Solutions through CAL Disaster Recovery As A Service
The unique integration of data protection, recovery, and cybersecurity into a single solution via a single web management console makes you more efficient. Keep your employees productive with instant availability with rapid failovers to the cloud, making your infrastructure resilient and cost-efficient. If your time or technical resources are stretched thin, let us know, and we’ll introduce you to one of our certified disaster recovery partners.
Solution reporting
Manage systems with ease using built-in monitoring tools like: a pre-integrated Prometheus engine and pre-configured Grafana dashboards, which show service state, availability, and performance.
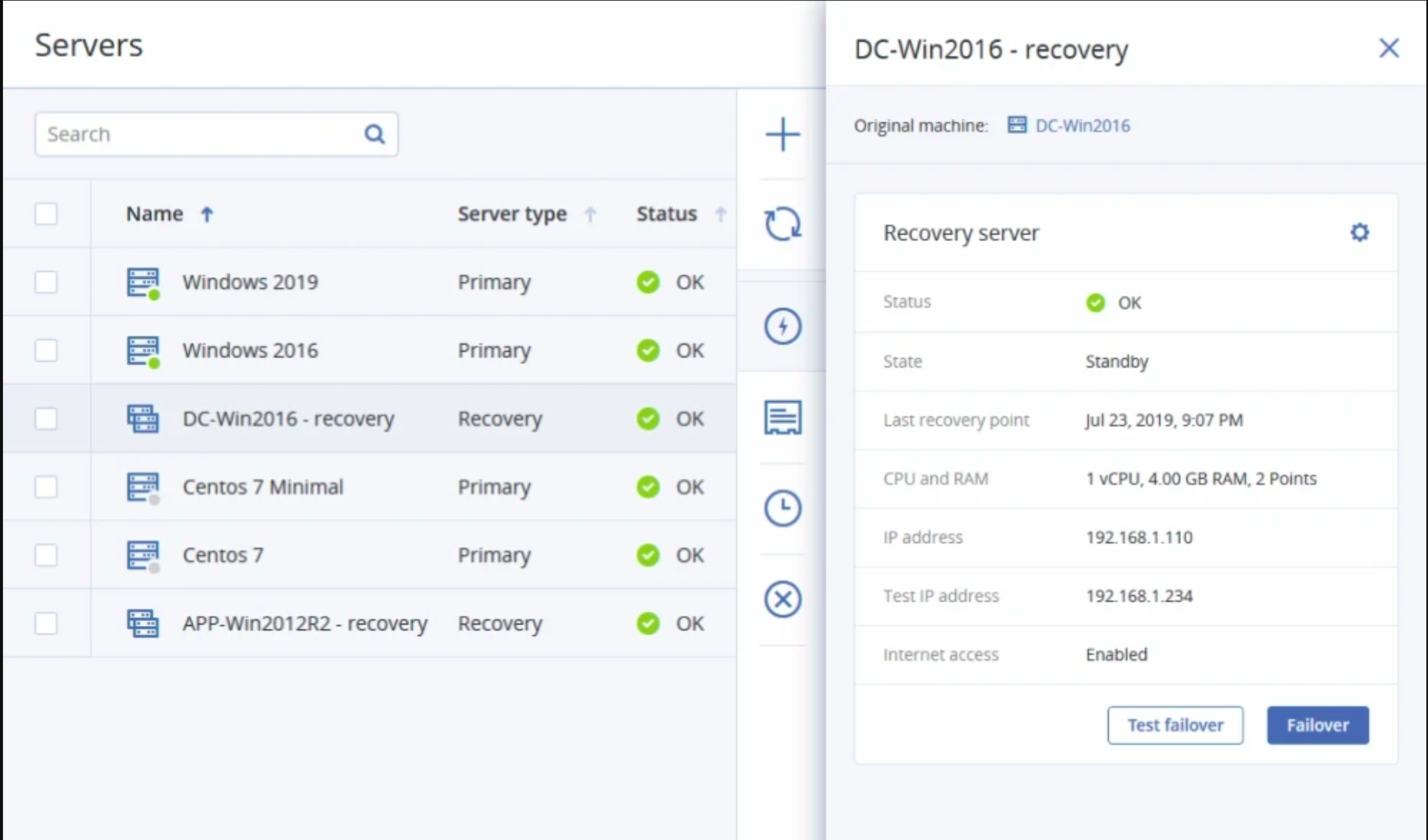
Runbook Orchestration
Automate key disaster recovery scenarios and ensure your systems will be recovered in the correct order to address inter dependencies between applications.
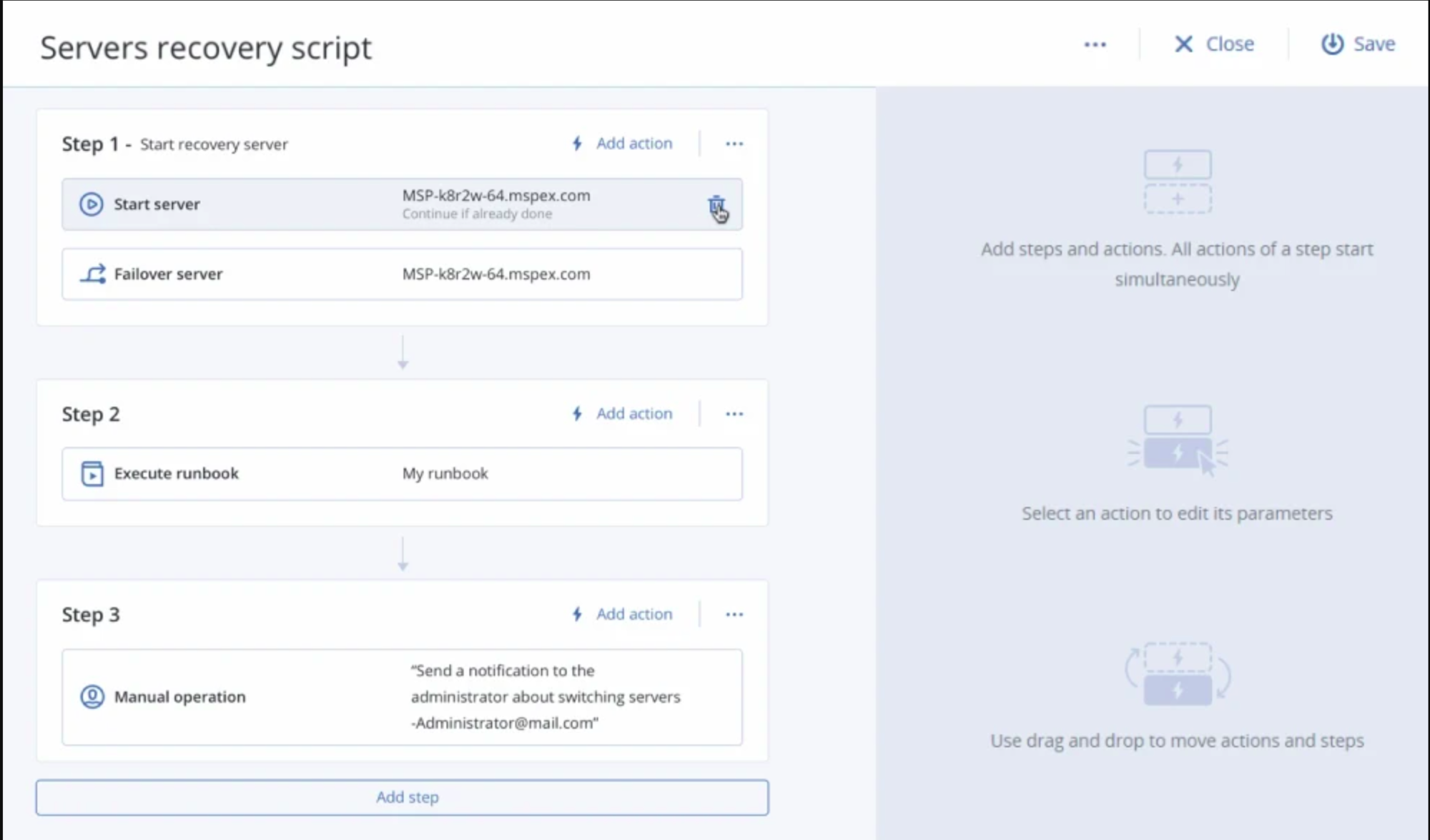
Under 15-minute RPOs and RTOs
Achieve both RPOs and RTOs that are under 15 minutes. The CAL RunVM engine enables best-in-class production and test failover speeds, while flexible backup frequency policies lead to tighter RPOs.
How to purchase ? Please contact us via chat or the contact form
Socials

Aerospace & Defense Company
Important
Our Industry
Government
National Security
Aerospace
Defense
Healthcare
Information Technology
Financial Services
Maritime
© Copyright 2022 . All Rights Reserved. Cyber Aeronautycs Ltd .
Registered in Bangladesh . Company Registration Number C-172611
